Government
Simplify citizen and staff access to protected systems - 2-second logins, no training needed!
more...Enterprise
Quickly fortify your systems against more than 100 normally difficult security problems.
more...Small Business
Solve more than 100 difficult security problems with one fast and simple solution.
more...Cloud and Hosting
Cloud and Hosting: Trust no one: CryptoPhoto's duty-separation architecture safely isolates all trust.
more...Crypto Currencies
Keep your crypto customers safe, even when sophisticated bad guys attack them hard.
more...Developers
Easily add high-strength logins and out-of-band digital signatures to your projects!
more...Defence
Quickly plug supplier security risks with one fast, easy, and comprehensive solution.
more...
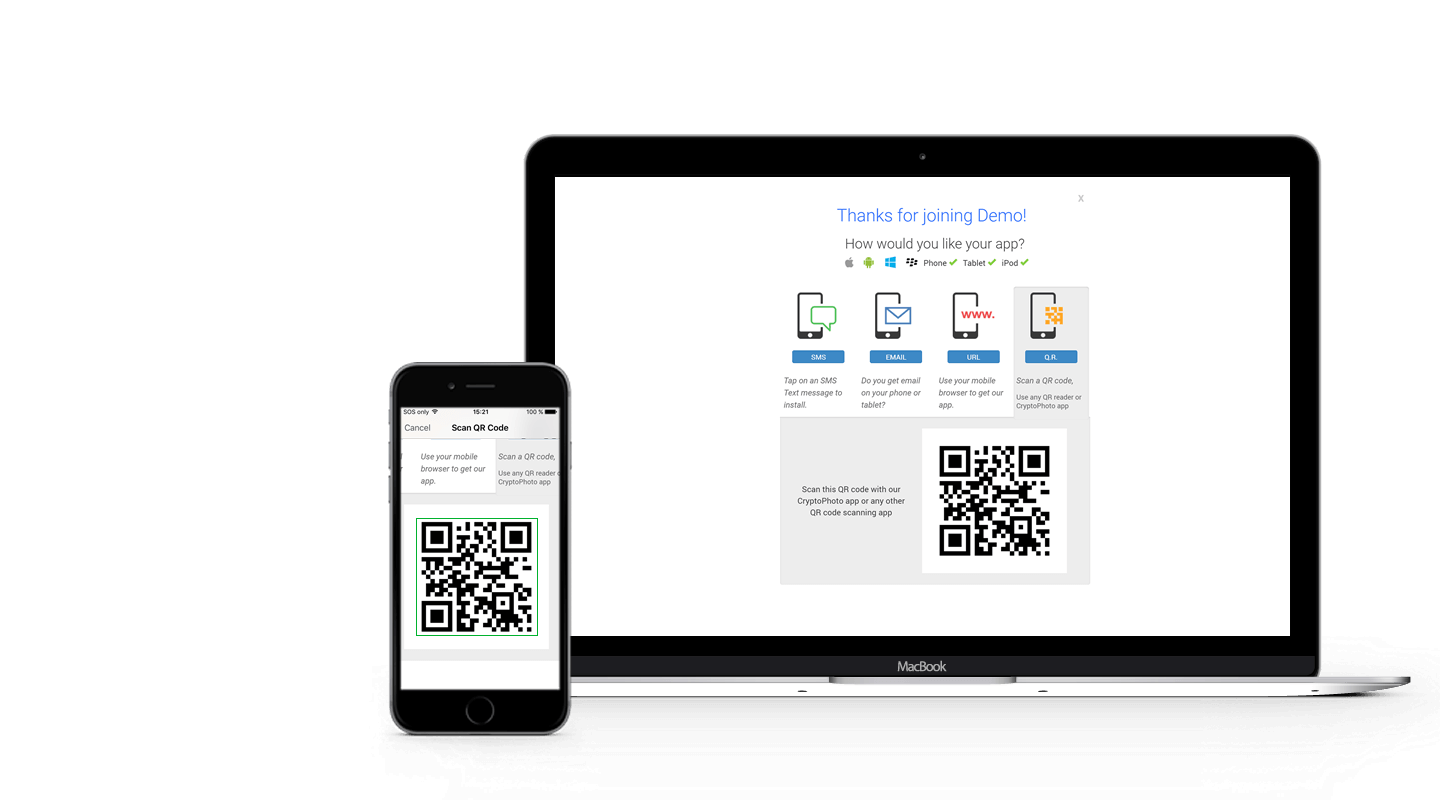
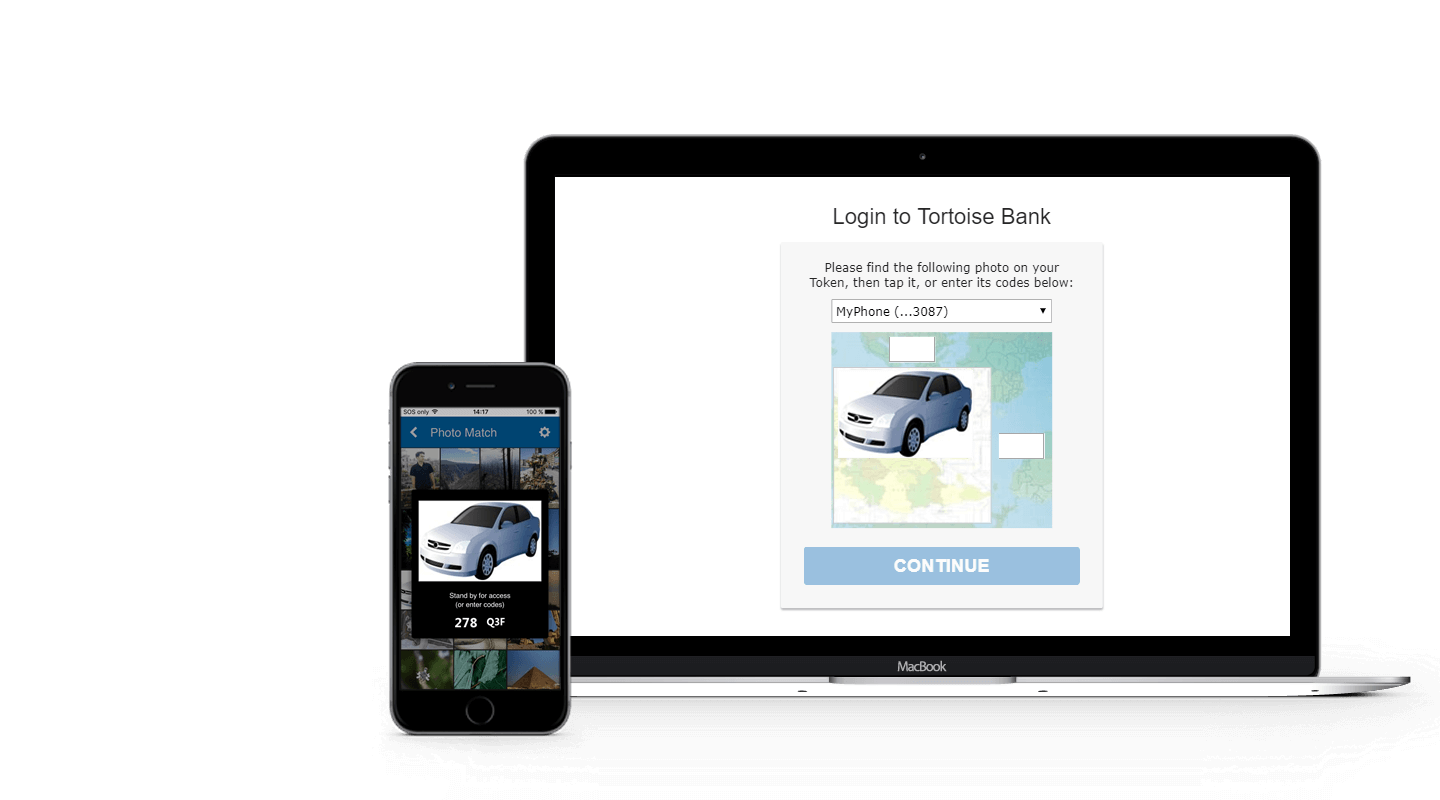
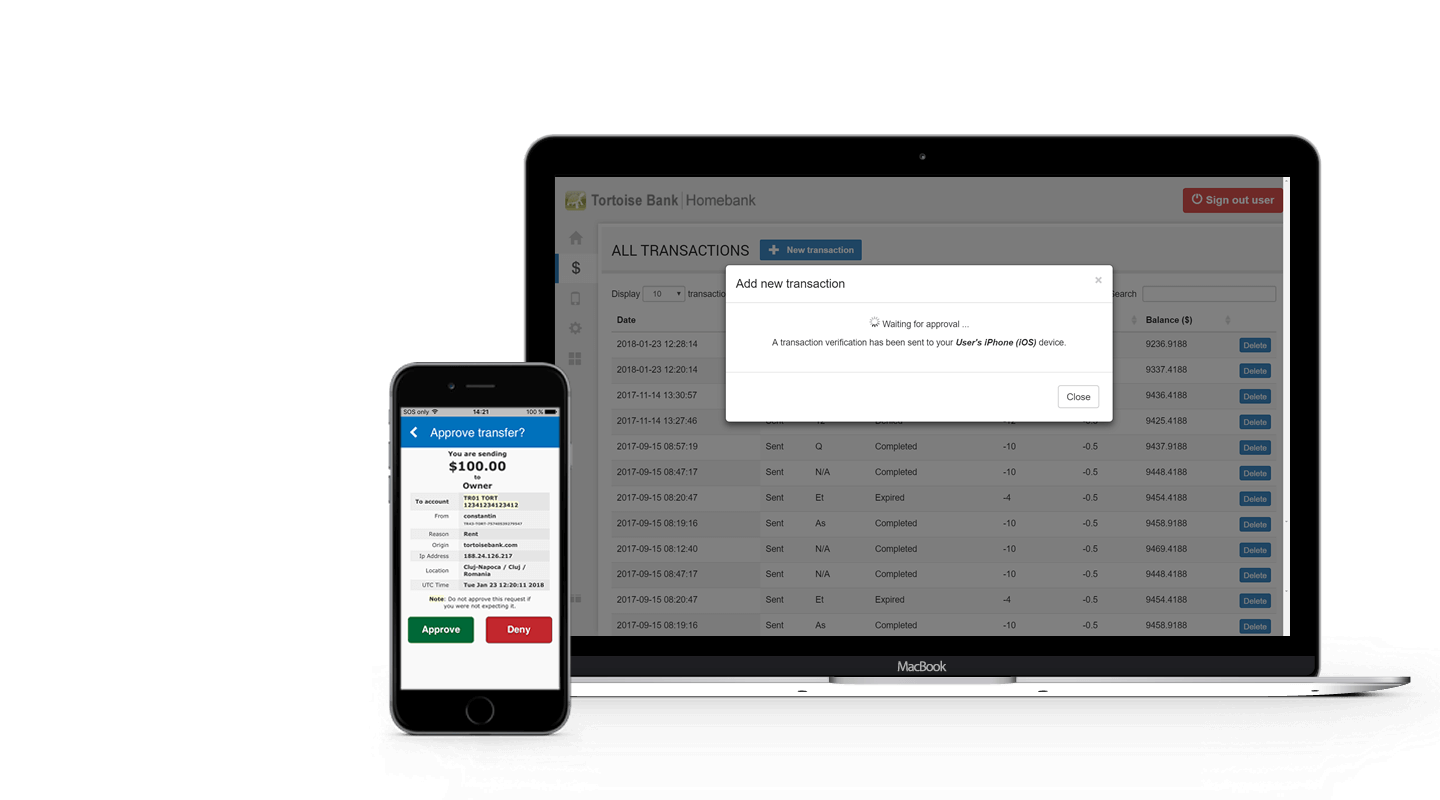
















 Loading ...
Loading ...